About Instahack
Instahack is a Bash and Python-based tool made to test password strength on Instagram accounts, using brute force techniques with Termux and Kali. It is designed to help users understand how weak passwords can be exploited and works by routing its activity through Tor for anonymity.
This tool is compatible with both rooted and non-rooted Android devices and can help users test their account security. Instahack was created by Waseem Akram and focuses on password testing for educational and ethical purposes. The tool is built using Bash and Python scripts.
How Does Instahack Work?
Instahack leverages Tor to change IP addresses, bypassing Instagram’s login limits to test large wordlists against a user’s password. The goal of this tool is to demonstrate how a brute force attack can expose vulnerabilities in weak passwords, so users can better protect themselves.
Advertisement
Instahack mimics Instagram APK signatures to avoid detection and maintains progress during network interruptions, ensuring continuous testing. This script can test up to 6 million passwords on a single account with minimal resources. However, improper Tor setup could leave users exposed, so proper configuration is essential.
Features of instahack
- Scripting for Security Testing
- Instagram Account Information Gathering
- Multi-threading for Faster Attacks
- Phishing Attack Capabilities
- Resumes Attacks: When the same wordlist is used on the same account
- Customization Options: Including multiple attack vectors
- Efficient Code: Built with Python requests, without selenium drivers
- Tor Identity Changes: Using the official Tor library, Stem
- Dumps successfully cracked accounts in the dump
Ethical Use and Disclaimer
Instahack is designed for ethical hacking and educational purposes to help users identify vulnerabilities in their accounts. Misuse of this tool for unauthorized hacking is illegal and violates Instagram’s terms of service.
Requirements for Running Instahack
requests, requests[socks], stem, tor, terminaltables
python3.8Watch a video
Unfortunately, the video tutorial has been removed by YouTube. Stay tuned for updates.🥲
Advertisement
Installation on Termux
To install Instahack on Termux, use the following single-line command:
wget https://raw.githubusercontent.com/evildevill/instahack/master/setup.sh && bash setup.shInstallation on Linux
To install Instahack on Linux, use the following single-line command:
wget https://raw.githubusercontent.com/evildevill/instahack/master/setup.sh && bash setup.shConfiguring Tor for Instahack
To configure Tor, open the Tor configuration file, typically located at /etc/tor/torrc:
Advertisement
sudo nano /etc/tor/torrcUncomment the ControlPort line by removing the # symbol, then save the file and restart Tor:
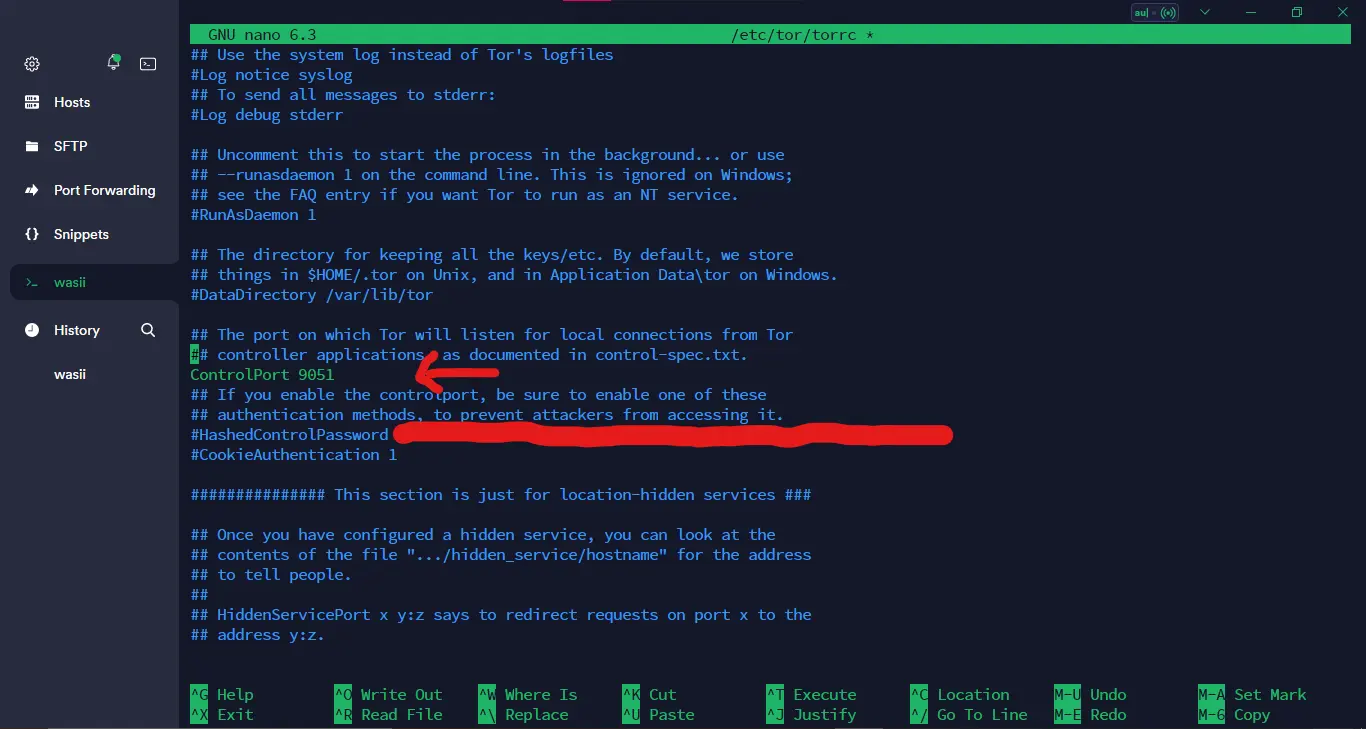
Now Save The file using CTRL + S and then exit using CTRL + X
Advertisement
Now generate instahack configuration file using.
instahack -cc -dcAfter creating the configuration file, navigate to the Instahack directory and execute the script:
bash instahack.shRunning Instahack and Purchasing License
Once you run the script, it will prompt you to enter a valid license key to continue. You can purchase an Instahack license via PayPal or card. After purchasing, enter your license key, select your options, and input the target username. Choose your wordlist, and the attack will begin.
Advertisement
If the password is successfully cracked, the tool will stop automatically and display the password.👻😉
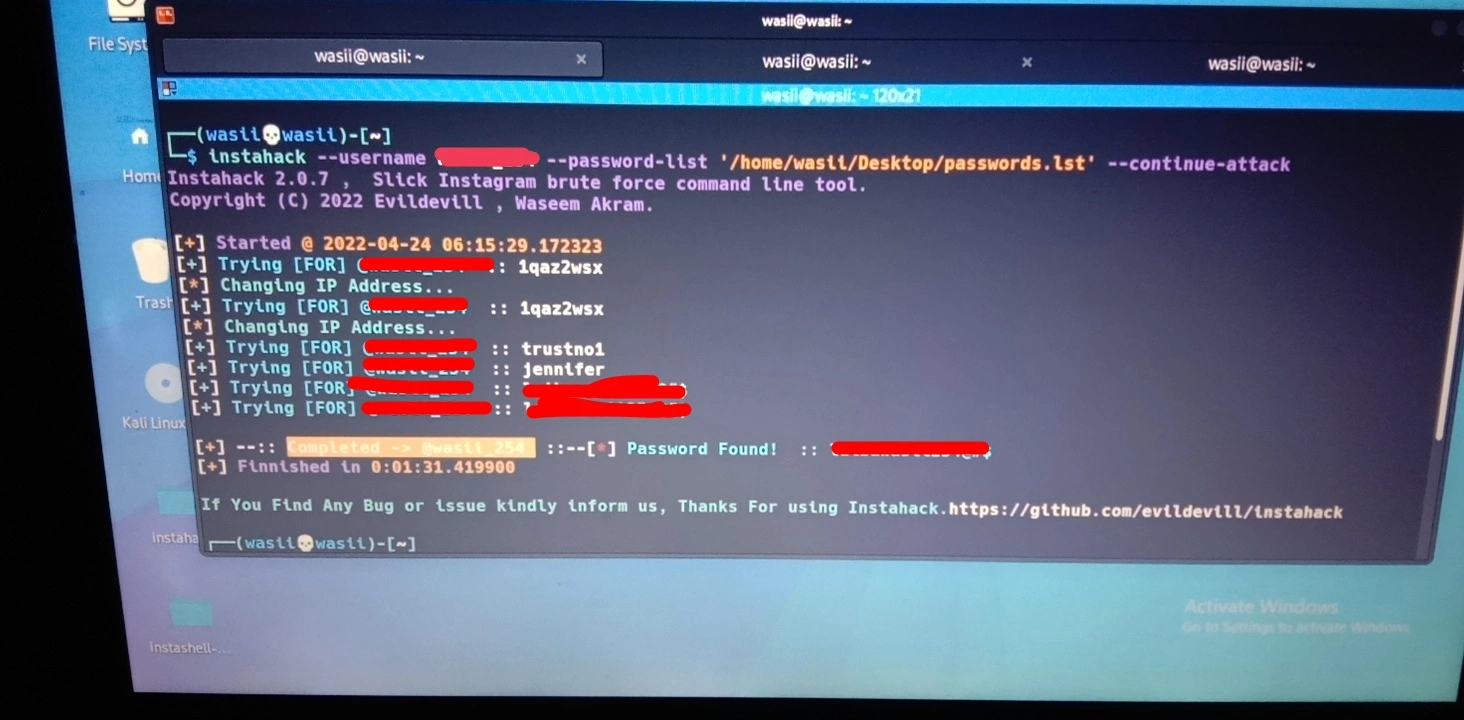
Finally 😍😘, we have successfully hack the target account
Advertisement
Get Instahack License
Buy Now
To access the full functionality of Instahack, you need a valid license. Purchase your license below:
Advertisement
How to Protect Your Instagram Account
Tips to Strengthen Your Password:
- Use a long password with a mix of uppercase, lowercase, numbers, and symbols.
- Enable Two-Factor Authentication (2FA) on Instagram to add an extra layer of security.
- Avoid using common or easily guessable passwords.
Why Weak Passwords Get Hacked:
Hackers use brute force attacks, like the ones simulated by Instahack, to test millions of password combinations in a short time. If your password is weak or commonly used, it could be cracked quickly.
To keep your account safe, regularly update your password and avoid reusing the same password across multiple sites.
Additional Security Measures:
- Regularly update your password and avoid using the same password across multiple accounts.
- Be cautious of phishing emails or messages that may attempt to steal your login credentials.
- Monitor your account activity for any suspicious logins or unauthorized access.
- Report any suspicious activity to Instagram and change your password immediately.
- Stay informed about the latest security threats and best practices to protect your account.
By following these security tips and staying vigilant, you can help safeguard your Instagram account from potential hacking attempts. Remember, protecting your online presence is essential in today’s digital age.
Advertisement
Stay safe and secure online!🔒🛡️
Advertisement



